NIST RMF 800-37 Rev 2
FRAMEWORKSLATEST POSTRISK FRAMEWORKS
Understanding the NIST Risk Management Framework: A Comprehensive Guide
Risk management is a critical component of any organization's cybersecurity strategy. The National Institute of Standards and Technology (NIST) has developed a robust Risk Management Framework (RMF) to help organizations manage and mitigate risks associated with information systems. This blog delves into the NIST RMF, its importance, key components, and the steps involved in its implementation.
Introduction
In today's digital age, organizations face numerous cyber threats that can compromise sensitive data and disrupt operations. To address these challenges, the NIST Risk Management Framework provides a structured process for managing risks related to information security. The RMF guides organizations through a series of steps to identify, assess, and mitigate risks, ensuring that information systems remain secure and resilient.
What is the NIST Risk Management Framework?
The NIST RMF is a comprehensive, flexible, and repeatable process designed to integrate security and risk management activities into the system development lifecycle. It emphasizes continuous monitoring and real-time risk assessment to adapt to evolving threats. The RMF is outlined in NIST Special Publication 800-37, which provides detailed guidance on its implementation.
Importance of the NIST RMF
Implementing the NIST RMF offers several benefits, including:
Enhanced Security: By following a structured approach, organizations can systematically address security risks and vulnerabilities.
Compliance: The RMF helps organizations comply with federal regulations and standards, such as the Federal Information Security Modernization Act (FISMA).
Informed Decision-Making: The framework provides a clear methodology for risk assessment, enabling informed decisions about security investments and resource allocation.
Continuous Improvement: The RMF's emphasis on continuous monitoring and assessment ensures that security measures evolve with changing threat landscapes.
Key Components of the NIST RMF
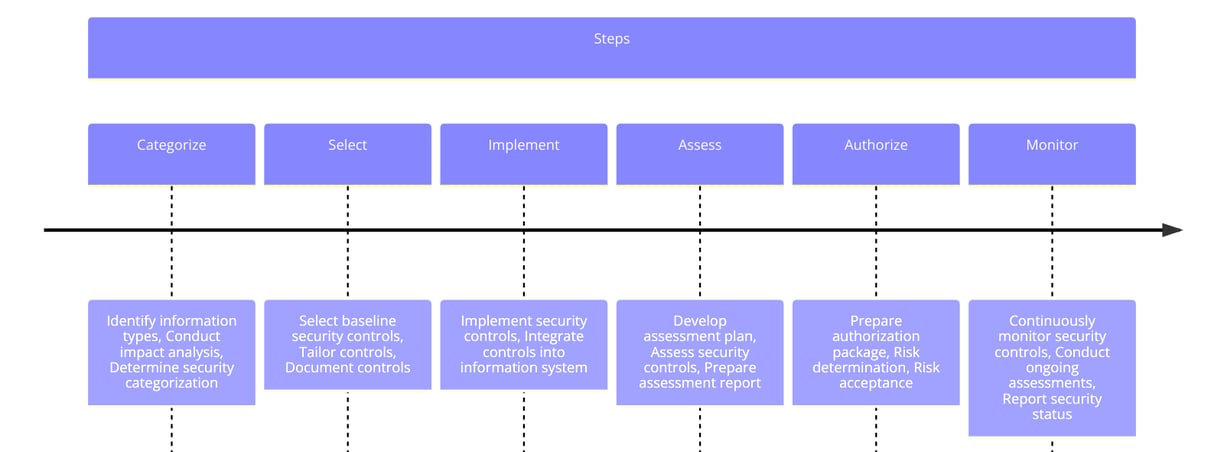
The NIST RMF consists of seven steps that guide organizations through the risk management process:
1. Prepare
2. Categorize
3. Select
4. Implement
5. Assess
6. Authorize
7. Monitor
Let's explore each step in detail.
1. Prepare
The preparation step involves establishing the context for risk management activities. This includes defining the organization's risk management strategy, identifying key stakeholders, and determining the scope of the RMF implementation. Preparation ensures that all subsequent steps are aligned with the organization's objectives and resources.
Key Activities:
Develop a risk management strategy
Identify and engage stakeholders
Define roles and responsibilities
Establish a governance structure
2. Categorise
In this step, organizations categorise their information systems based on the potential impact of a security breach. The categorization is performed using criteria outlined in NIST Special Publication 800-60, which helps determine the level of risk associated with each system.
Key Activities:
Identify the information types processed by the system
Determine the security impact level (low, moderate, or high)
Document the categorization results
3. Select
After categorizing the information systems, organizations select appropriate security controls to mitigate identified risks. The controls are chosen from the NIST Special Publication 800-53, which provides a comprehensive catalog of security and privacy controls.
Key Activities:
Select baseline controls based on system categorization
Tailor controls to meet specific organizational needs
Develop a security plan outlining the selected controls
4. Implement
In the implementation step, organizations apply the selected security controls to their information systems. This involves configuring and deploying technical, administrative, and physical controls to protect the system and its data.
Key Activities:
Implement the security controls as specified in the security plan
Document the implementation details
Ensure controls are functioning as intended
5. Assess
Once the controls are implemented, they must be assessed to ensure they are effective in mitigating risks. This step involves evaluating the controls' design and operational effectiveness through testing and evaluation.
Key Activities:
Develop an assessment plan
Conduct control assessments
Document assessment findings
Address any identified deficiencies
6. Authorize
Authorization is the process of formally accepting the risk associated with the information system. Senior management reviews the assessment results and decides whether the system's risk is acceptable for operation.
Key Activities:
Prepare an authorization package, including the security plan, assessment report, and risk assessment
Senior management reviews the package
Issue an authorization decision (approval, denial, or conditional approval)
7. Monitor
The final step involves continuously monitoring the information system and its environment to detect changes that could affect security. Continuous monitoring ensures that security controls remain effective and that new risks are promptly addressed.
Key Activities:
Implement a continuous monitoring strategy
Track security control effectiveness
Conduct regular assessments and audits
Update the security plan and controls as necessary
Conclusion
The NIST Risk Management Framework is an essential tool for organizations seeking to manage cybersecurity risks effectively. By following its structured approach, organizations can ensure their information systems are secure, compliant, and resilient against evolving threats. Implementing the RMF not only enhances security but also supports informed decision-making and continuous improvement in risk management practices.
In summary, the seven steps of the NIST RMF—Prepare, Categorize, Select, Implement, Assess, Authorize, and Monitor—provide a comprehensive roadmap for managing risks in today's complex cybersecurity landscape. By adopting the RMF, organizations can build robust security programs that safeguard their critical assets and maintain trust with stakeholders.