NIST Cybersecurity Framework (CSF
RISK FRAMEWORKSLATEST POSTFRAMEWORKS
In today's digital age, cybersecurity is a critical concern for organizations of all sizes and industries. Cyber threats continue to evolve, becoming more sophisticated and potentially more damaging. To combat these threats, organizations need a robust and flexible cybersecurity strategy. The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) provides a comprehensive guide to help organizations manage and reduce cybersecurity risk. This blog will explore the key aspects of the NIST CSF, its components, and how it can benefit organizations.
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework, initially released in 2014 and updated periodically, is a set of guidelines, standards, and best practices designed to help organizations manage cybersecurity risks. It is a voluntary framework that provides a flexible approach for organizations to assess and improve their ability to prevent, detect, and respond to cyber incidents.
Key Components of the NIST CSF
The NIST CSF is composed of three main components: the Framework Core, the Framework Implementation Tiers, and the Framework Profile. Each of these components plays a crucial role in helping organizations develop a comprehensive cybersecurity strategy.
1. Framework Core
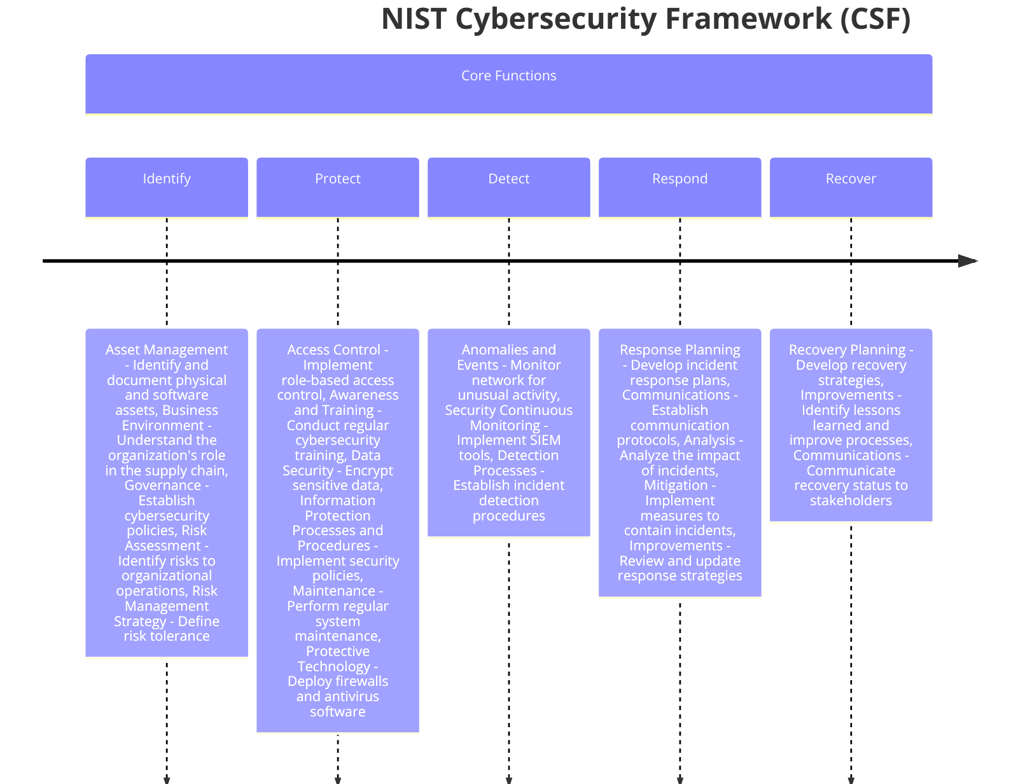
The Framework Core is the heart of the NIST CSF. It consists of five high-level functions: Identify, Protect, Detect, Respond, and Recover. These functions represent the essential elements of a robust cybersecurity program and are further divided into categories and subcategories, providing a detailed approach to managing cybersecurity risk.
Identify: This function helps organizations understand their cybersecurity risks by identifying critical assets, systems, and data. It involves creating an inventory of hardware and software, understanding the organization's risk management strategy, and identifying vulnerabilities and threats.
Protect: The Protect function focuses on implementing safeguards to ensure the delivery of critical infrastructure services. This includes access control, data security, protective technology, and employee training and awareness.
Detect: This function is about developing and implementing activities to identify the occurrence of a cybersecurity event. It involves continuous monitoring, anomaly detection, and security event analysis to detect potential threats.
Respond: The Respond function outlines the steps to take once a cybersecurity incident is detected. This includes incident response planning, communication, analysis, mitigation, and improvements to prevent future incidents.
Recover: The final function focuses on restoring normal operations after a cybersecurity incident. It includes recovery planning, improvements based on lessons learned, and communication with stakeholders.
2. Framework Implementation Tiers
The Framework Implementation Tiers provide context on how an organization views cybersecurity risk and the processes in place to manage that risk. There are four tiers, each representing a different level of maturity and integration of cybersecurity practices within the organization.
Tier 1: Partial: Organizations at this tier have an ad hoc and reactive approach to cybersecurity. There is limited awareness of cybersecurity risks, and processes are not standardized or formalized.
Tier 2: Risk Informed: At this tier, organizations have some awareness of cybersecurity risks and have begun to establish risk management practices. However, these practices may not be consistently applied across the organization.
Tier 3: Repeatable: Organizations at this tier have standardized and well-documented cybersecurity practices. There is a clear understanding of cybersecurity risks, and risk management processes are consistently applied.
Tier 4: Adaptive: This tier represents the highest level of cybersecurity maturity. Organizations are proactive in their approach to cybersecurity, continuously improving their processes based on lessons learned and threat intelligence.
3. Framework Profile
The Framework Profile is a customized alignment of the Framework Core categories and subcategories with the organization's business requirements, risk tolerance, and resources. It helps organizations identify and prioritize opportunities for improving their cybersecurity posture. The Profile is used to create a roadmap for reducing cybersecurity risk that is tailored to the organization's specific needs and objectives.
Benefits of Implementing the NIST CSF
Implementing the NIST CSF offers several benefits for organizations, regardless of their size or industry. Here are some of the key advantages:
1. Improved Risk Management
The NIST CSF provides a structured approach to identifying, assessing, and managing cybersecurity risks. By following the framework, organizations can better understand their risk landscape and implement appropriate measures to mitigate those risks.
2. Enhanced Communication
The framework offers a common language for discussing cybersecurity risks and practices, facilitating better communication between technical and non-technical stakeholders. This can help ensure that everyone in the organization understands the importance of cybersecurity and their role in maintaining it.
3. Increased Resilience
By following the NIST CSF, organizations can improve their ability to detect, respond to, and recover from cybersecurity incidents. This can reduce the impact of such incidents and help ensure the continuity of critical operations.
4. Regulatory Compliance
Many regulatory bodies reference the NIST CSF in their cybersecurity requirements. By implementing the framework, organizations can more easily demonstrate compliance with relevant regulations and standards.
5. Scalability and Flexibility
The NIST CSF is designed to be flexible and scalable, making it suitable for organizations of all sizes and industries. It can be tailored to meet the specific needs and risk tolerance of each organization, allowing for a customized approach to cybersecurity.
Steps to Implement the NIST CSF
Implementing the NIST CSF involves several key steps:
1. Establish a Leadership Commitment: Secure commitment from top management to prioritize cybersecurity and allocate necessary resources.
2. Assess Current State: Conduct a thorough assessment of the organization's current cybersecurity practices and identify gaps and areas for improvement.
3. Develop a Target Profile: Create a customized Framework Profile that aligns with the organization's business objectives, risk tolerance, and resources.
4. Create a Roadmap: Develop a roadmap for achieving the target profile, including specific actions, timelines, and responsibilities.
5. Implement and Monitor: Implement the roadmap and continuously monitor progress, making adjustments as needed based on changing threats and business needs.
6. Review and Improve: Regularly review and update the cybersecurity program to ensure it remains effective and aligned with the organization's goals.
Conclusion
The NIST Cybersecurity Framework is a powerful tool for organizations seeking to improve their cybersecurity posture. By providing a structured and flexible approach to managing cybersecurity risks, the NIST CSF helps organizations protect their critical assets, detect and respond to incidents, and recover from disruptions. Implementing the NIST CSF can enhance communication, increase resilience, and ensure compliance with regulatory requirements, ultimately leading to a more secure and robust cybersecurity environment. Whether your organization is just beginning its cybersecurity journey or looking to enhance an existing program, the NIST CSF offers valuable guidance and best practices to help you achieve your goals.