ISO 27005
RISK FRAMEWORKSLATEST POSTINFOSEC BASICS
6/29/20244 min read
In today's digital age, managing information security risks is critical for organizations of all sizes. The ISO/IEC 27005 standard provides comprehensive guidelines for managing information security risks, helping organizations protect their valuable data assets. This blog delves into the key aspects of ISO 27005, its importance, structure, and how it can benefit organizations in managing information security risks effectively.
What is ISO 27005?
ISO/IEC 27005 is an international standard published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It is part of the ISO/IEC 27000 family of standards, which focuses on information security management systems (ISMS). Specifically, ISO 27005 provides guidelines for information security risk management and is designed to help organizations identify, assess, and mitigate information security risks.
Importance of ISO 27005
Effective information security risk management is essential for protecting an organization's data and maintaining trust with customers, partners, and stakeholders. ISO 27005 is important for several reasons:
Systematic Approach: It provides a structured methodology for identifying and managing information security risks, ensuring a consistent approach across the organization.
Compliance: Adopting ISO 27005 can help organizations comply with legal, regulatory, and contractual requirements related to information security.
Risk Awareness: It enhances awareness of information security risks within the organization, promoting a culture of security.
Resource Allocation: Helps prioritize risks based on their potential impact, ensuring efficient allocation of resources to mitigate the most significant threats.
Structure of ISO 27005
ISO 27005 is structured into several key sections that guide organizations through the process of information security risk management. Here is an overview of its main components:
Introduction and Scope
The standard begins with an introduction that outlines its purpose and scope, emphasizing its role in supporting the requirements of an ISMS as specified in ISO/IEC 27001.
Normative References
This section lists other standards and documents referenced within ISO 27005, such as ISO/IEC 27001 and ISO/IEC 27002.
Terms and Definitions
Key terms and definitions used throughout the standard are provided to ensure a clear understanding of the concepts discussed.
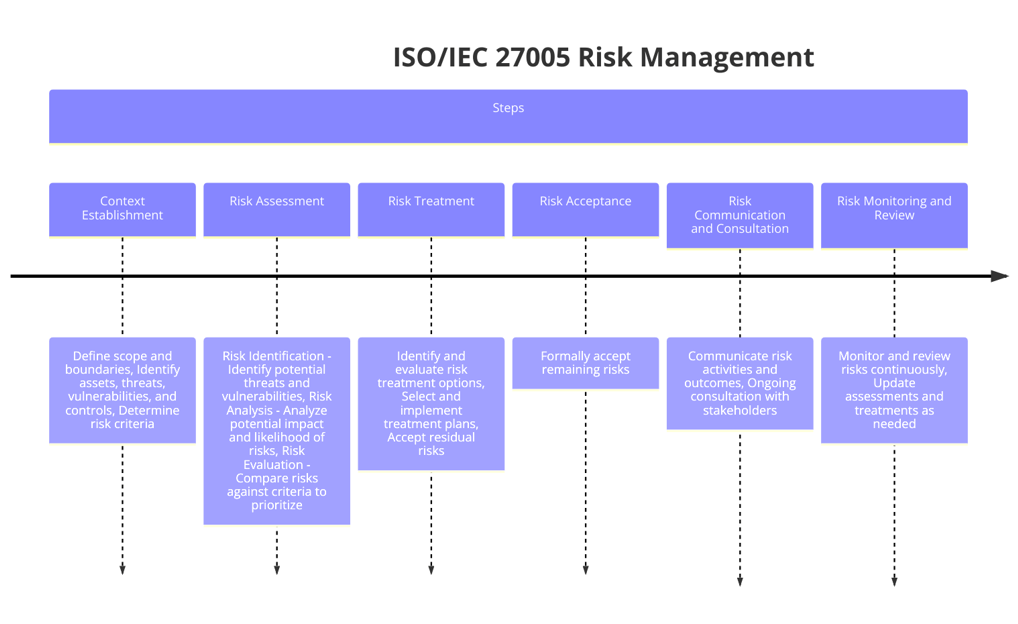
Overview of the Risk Management Process
This section provides a high-level overview of the information security risk management process, including risk assessment, risk treatment, risk acceptance, and risk communication.
Risk Assessment
Risk Identification: Identifying assets, threats, vulnerabilities, and potential impacts.
Risk Analysis: Assessing the likelihood and consequences of identified risks.
Risk Evaluation: Comparing risk levels against risk criteria to determine the significance of the risks.
Risk Treatment
Risk Reduction: Implementing controls to reduce the likelihood or impact of risks.
Risk Retention: Accepting the risk when it is within the organization's risk tolerance.
Risk Avoidance: Avoiding activities that lead to risk exposure.
Risk Transfer: Transferring the risk to another party, such as through insurance.
Risk Acceptance
This section discusses the criteria and processes for accepting residual risks after treatment.
Risk Communication and Consultation
Emphasises the importance of communicating and consulting with stakeholders throughout the risk management process.
Risk Monitoring and Review
Guidelines for ongoing monitoring and review of risks and the effectiveness of risk treatment measures.
Implementing ISO 27005
Implementing ISO 27005 involves several steps that organizations can follow to integrate effective risk management practices into their ISMS:
Establish the Context
Define the scope and boundaries of the risk management process.
Identify stakeholders and their information security requirements.
Set the risk criteria, including risk appetite and tolerance levels.
Conduct Risk Assessment
Identify assets, threats, and vulnerabilities.
Analyze and evaluate the risks based on their likelihood and impact.
Prioritize risks to determine which require treatment.
Develop Risk Treatment Plans
Select appropriate risk treatment options, such as implementing controls or transferring risks.
Develop action plans for each identified risk, specifying responsibilities, timelines, and resources.
Implement Risk Treatments
Execute the risk treatment plans by implementing controls and other measures.
Ensure that risk treatments are integrated into the organization's operations and processes.
Monitor and Review
Continuously monitor the risk environment and the effectiveness of risk treatments.
Review and update risk assessments and treatment plans regularly or when significant changes occur.
Communicate and Consult
Maintain ongoing communication and consultation with stakeholders about risk management activities and decisions.
Benefits of ISO 27005
Adopting ISO 27005 offers numerous benefits to organizations, including:
Enhanced Security Posture
By systematically identifying and managing risks, organizations can strengthen their overall security posture and reduce the likelihood of security incidents.
Improved Compliance
Following ISO 27005 guidelines helps organizations meet various legal, regulatory, and contractual requirements related to information security.
Risk-Based Decision Making
ISO 27005 promotes a risk-based approach to decision making, enabling organizations to prioritize security investments based on the most significant risks.
Stakeholder Confidence
Demonstrating a commitment to effective risk management can enhance stakeholder confidence and trust in the organization's ability to protect sensitive information.
Resource Optimization
By focusing on the most critical risks, organizations can allocate resources more effectively, ensuring that security efforts are targeted where they are needed most.
Conclusion
In an era where information security threats are constantly evolving, managing risks effectively is more important than ever. ISO/IEC 27005 provides a comprehensive framework for organizations to identify, assess, and mitigate information security risks, ensuring the protection of valuable data assets. By adopting ISO 27005, organizations can enhance their security posture, achieve compliance, and build trust with stakeholders, ultimately supporting their overall business objectives. Implementing this standard requires a systematic approach, ongoing monitoring, and continuous improvement, but the benefits it offers make it a worthwhile investment for any organization committed to information security.