Cryptographic Hashes: The Digital Fingerprints Securing Our Data
INFOSEC BASICSLATEST POST
Introduction
Ever wondered how your online data remains intact and secure even as it travels across the vast expanse of the internet? Imagine if every piece of data had a unique fingerprint, ensuring it couldn’t be tampered with without being detected. Welcome to the world of cryptographic hashes, the unsung heroes of digital security. From verifying downloaded files to securing online transactions, cryptographic hashes play a crucial role in maintaining the integrity and authenticity of digital information. In this blog, we’ll dive into what cryptographic hashes are, how they work, their importance, applications, and real-world examples that illustrate their significance.
What Are Cryptographic Hashes?
In the simplest terms, a cryptographic hash is a special kind of digital fingerprint. When data is fed into a hash function, it produces a fixed-size string of characters, typically a hexadecimal number, that uniquely represents the input data. Here’s what makes these hashes truly special:
- Fixed Size: Regardless of the input size, the output hash is always the same length. For instance, whether you hash a single word or an entire novel, the output using SHA-256 will always be a 64-character string.
- Deterministic: The same input will always yield the same hash. Change even a single character, and the hash will change drastically.
- Uniqueness: It's extremely unlikely for two different inputs to produce the same hash, a property known as collision resistance.
Cryptographic hashes are designed to be quick and efficient, making them ideal for various applications that require rapid data verification. But before we delve deeper into their applications, let's understand how these hashes are generated.
How Do Cryptographic Hashes Work?
Think of a cryptographic hash function as a sophisticated blender. You put your ingredients (data) into the blender, and it whirs them around to produce a smooth, consistent output (the hash). No matter how you arrange the ingredients in the blender, if they’re the same ingredients, you’ll get the same smoothie every time.
1. Input Data: Anything you want to hash—a password, a file, a message.
2. Hash Function: This is the blender – SHA-256, MD5, SHA-1, etc.
3. Output Hash: The smoothie – a fixed-size string that looks nothing like the input.
Underneath, these hash functions perform complex mathematical operations to ensure the output appears random and is securely bound to the input data. Let’s break down the process:
1. Preprocessing: The input data is first prepared through padding and splitting into blocks. Padding ensures that the input length is suitable for the hashing algorithm.
2. Initial Hash Value: Hash algorithms start with an initial hash value, often derived from mathematical constants.
3. Compression Function: Each block of input data is processed through a series of complex operations (like bitwise operations, modular additions, and logical functions) to produce intermediate hash values.
4. Final Hash Value: After processing all blocks, the final hash value is produced, representing the entire input data uniquely.
These steps ensure that even a tiny change in the input data results in a significantly different hash output, a property known as the avalanche effect. This characteristic is crucial for maintaining the security and reliability of cryptographic hashes.
Importance and Applications
Why are cryptographic hashes so important? Their applications are vast and vital to our digital lives:
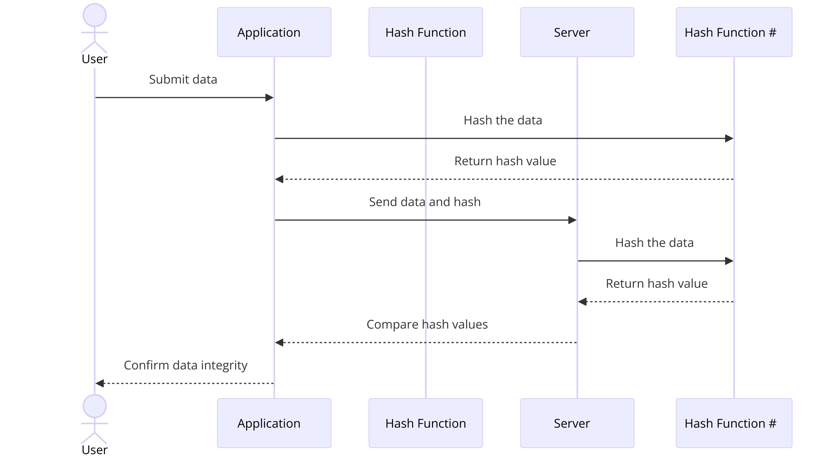
- Data Integrity: Hashes verify that data hasn't been altered. When you download software, a hash can confirm it hasn’t been corrupted or tampered with during transmission. This is essential for maintaining the integrity of files, ensuring they are exactly as intended by the original creator.
- Password Storage: Instead of storing actual passwords, systems store the hash of the password. When you log in, the system hashes your input and compares it to the stored hash. This way, even if the database is compromised, the actual passwords remain secure. Hash functions used in password storage often include salting, where a unique value is added to each password before hashing to prevent attackers from using precomputed tables (rainbow tables) to crack passwords.
- Digital Signatures: Hashes ensure that a digital document remains unaltered. If any change is made, the hash changes, alerting to potential tampering. Digital signatures involve hashing the document and then encrypting the hash with a private key, providing both integrity and authenticity.
- Blockchain Technology: Each block in a blockchain contains the hash of the previous block, creating a secure, immutable chain of data. This ensures that any alteration in a block would change its hash, breaking the chain and making tampering evident. Cryptographic hashes are fundamental to the security and integrity of blockchain and cryptocurrency systems.
- File Verification: When you download a file, such as software or an update, websites often provide a hash value. After downloading, you can run the same hash function on the file to verify its integrity. If the hashes match, the file is authentic and unaltered.
These applications highlight the crucial role cryptographic hashes play in maintaining the security and integrity of digital information across various platforms and technologies.
Popular Cryptographic Hash Algorithms
Several cryptographic hash algorithms are widely used, each with its own strengths and weaknesses. Here are some of the most popular ones:
1. MD5 (Message Digest Algorithm 5): Once a popular choice, MD5 produces a 128-bit hash value. However, due to vulnerabilities and the ability to produce collisions (where two different inputs produce the same hash), it is now considered insecure for most applications.
2. SHA-1 (Secure Hash Algorithm 1): SHA-1 produces a 160-bit hash value and was widely used for secure data transmission. However, it also has vulnerabilities, and its use is now discouraged in favor of more secure algorithms.
3. SHA-256 (Secure Hash Algorithm 256-bit): Part of the SHA-2 family, SHA-256 produces a 256-bit hash value and is currently one of the most secure and widely used hash functions. It is extensively used in blockchain technology and secure data transmission.
The evolution of hash algorithms reflects the ongoing battle between security experts and attackers, with newer algorithms being developed to address vulnerabilities in older ones.
Security Considerations
Despite their strengths, cryptographic hashes are not immune to attacks. Key vulnerabilities include:
- Collision Attacks: Finding two different inputs that produce the same hash. While rare, collision attacks can undermine the security of a hash function. Algorithms like MD5 and SHA-1 have known collision vulnerabilities.
- Length Extension Attacks: Exploiting certain properties of hash functions to extend the length of the input message while maintaining the same hash. This type of attack is possible in some hash functions if the internal state is exposed.
Best practices for using cryptographic hashes include:
- Use Strong Hash Functions: Avoid outdated functions like MD5 and SHA-1. Instead, use SHA-256 or members of the SHA-3 family, which offer better security and collision resistance.
- Salting Passwords: Add a unique value (salt) to each password before hashing to prevent attackers from using precomputed tables to crack passwords.
- Regularly Update: Stay informed about advancements in cryptographic research to ensure continued security. As new vulnerabilities are discovered, it's essential to transition to more secure hash functions and update systems accordingly.
By adhering to these best practices, organizations and individuals can better protect their digital data and maintain the integrity and security of their information systems
Real-World Examples
Let’s bring these concepts to life with some real-world examples:
1. Blockchain Security: In cryptocurrencies like Bitcoin, cryptographic hashes secure transaction data. Each block in the chain includes the hash of the previous block, making it virtually impossible to alter any information without disrupting the entire chain. This ensures the integrity and immutability of the blockchain.
2. File Verification: When you download software from a reputable source, you might see a hash value provided alongside the download link. After downloading the file, you can use a hash function to generate its hash and compare it to the provided value. If the hashes match, the file is authentic and hasn't been tampered with.
3. Password Protection: Think of your favorite social media platform. When you create a password, the platform hashes it before storing it. When you log in, the entered password is hashed and compared to the stored hash. This method ensures that even if hackers access the database, they only get the hashed passwords, not the actual ones.
These examples illustrate how cryptographic hashes are integral to the security and integrity of various digital systems and applications.
Conclusion
Cryptographic hashes are the silent sentinels guarding our digital realms. From verifying data integrity to securing blockchain transactions, their applications are both diverse and crucial. As technology advances, so too will the methods of cryptographic hashing, continuously enhancing our digital security.
In a world increasingly dependent on digital interactions, understanding the basics of cryptographic hashes empowers us to appreciate the complex mechanisms protecting our data. So next time you download a file or log into your favourite app, remember the powerful digital fingerprints working behind the scenes to keep your information safe.
By grasping the importance and mechanics of cryptographic hashes, we can better navigate and secure our digital future. Stay curious, stay informed, and appreciate the intricate technologies that make our online experiences safe and seamless. Understanding cryptographic hashes not only enhances our digital literacy but also helps us make informed decisions about the security measures we employ in our personal and professional lives.